With the rapid development of the Internet of Things (IoT), the proliferation of smart devices is transforming our lives at an unprecedented pace. From smart speakers at home to industrial monitoring systems, IoT devices have penetrated every aspect of our daily lives. However, while these devices bring convenience, they also pose serious security and privacy challenges. IoT devices frequently collect and transmit sensitive data, and if not properly protected, this data could be at great risk, potentially leading to severe privacy leaks and security threats.

The Risks of Sensitive Data in IoT
IoT devices are capable of continuously collecting data, including users’ location information, personally identifiable information (PII), health data, and even corporate secrets. This sensitive data is often transmitted via wireless networks, and if left unprotected, it may become a target for cyberattacks. Once stolen, hackers can use this data for identity theft, corporate espionage, or malicious disruption, leading to severe consequences for individuals, businesses, and even national security.
The number of IoT devices is increasing every day, and the volume of data they generate is growing exponentially. This data overload not only puts unprecedented pressure on enterprise security systems but also makes it more difficult to identify security threats. Traditional security systems often struggle to process such vast amounts of data in real time, let alone detect potential threats in a timely manner.
Security Challenges Brought by Data Overload
IoT devices produce massive amounts of data due to their nature. Each smart device in a household, every surveillance device in a company, and every sensor in industrial production continuously generate and transmit large amounts of data. As this data flows to the cloud for processing and analysis, it increases the burden on enterprise networks. If security systems are not updated or expanded in time, their ability to identify and respond to security threats will be significantly reduced.
Moreover, as data volumes surge, noise data (non-critical or invalid data) also increases, making it more difficult to identify real threats. In such cases, security systems often rely on artificial intelligence and machine learning algorithms to analyze and filter large-scale data, ensuring accurate detection of malicious activity from within the flood of information.
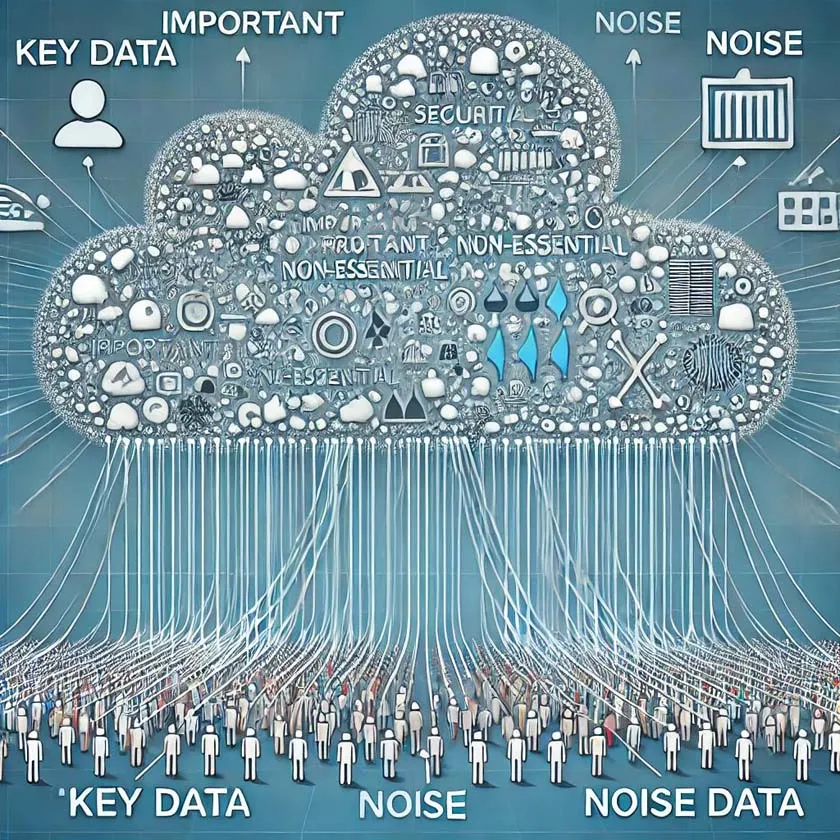
Weaknesses in Current IoT Technology
Currently, many IoT devices are not designed with security as a priority. Many devices come with default, insecure passwords or lack encryption features altogether. This means that once installed and connected to the network, these devices can easily become targets for attackers. This weakness in security control not only increases the risk of data breaches but also makes it easier for malware or attackers to take control of these devices, leading to more severe consequences.
In addition to generating data at the edge of the network, IoT devices often passively collect information. Many users may not even realize that they have authorized devices to access their sensitive data. This passive data collection makes privacy breaches more subtle and harder to detect. For businesses, the absence of effective data monitoring and alert systems means that data breaches often go unnoticed until after the damage has been done, by which point the losses may be irreparable.
How to Protect Sensitive Data in IoT
Facing the information overload and privacy crisis brought by IoT devices, adopting effective security measures is crucial. Here are some key strategies to help businesses and individuals better protect sensitive data in IoT devices:
1. Data Encryption: Encrypt all data generated by IoT devices to ensure that even if intercepted during transmission, the data cannot be read. This can be achieved through technologies such as end-to-end encryption (E2EE) or virtual private networks (VPN).
2. Multi-layer Security Architecture: Adopt a multi-layered security architecture with protective measures deployed from the device to the cloud. This ensures that even if one layer is compromised, the overall security remains intact. For example, strong access controls should be deployed at the device level, while encryption and backup should be enabled in the cloud.
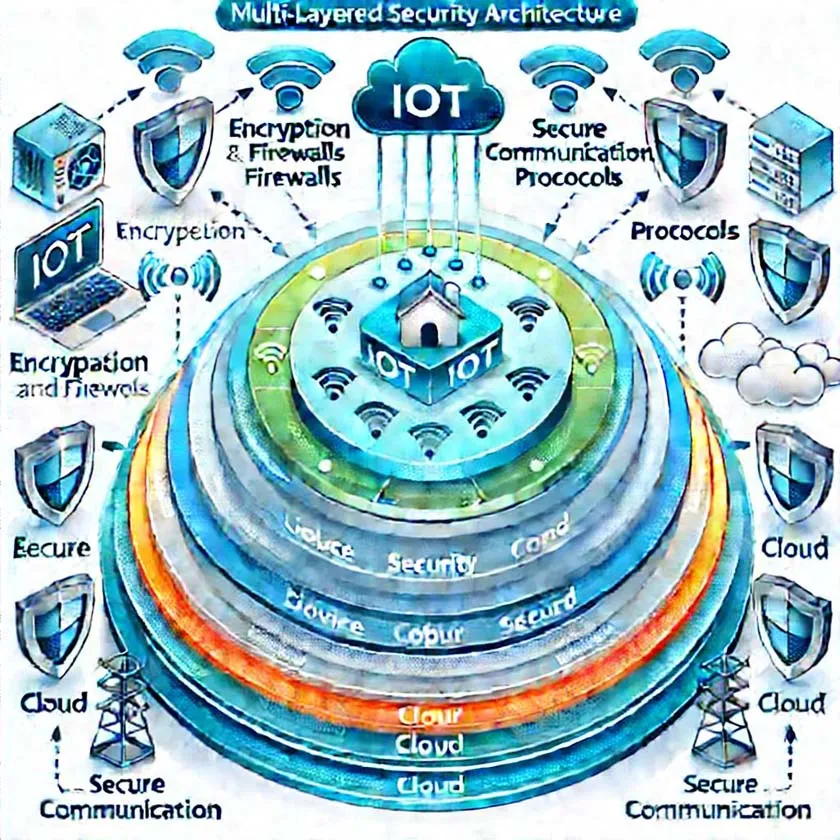
3. Regular Updates and Patch Management: IoT device manufacturers should provide regular security updates and patches, and users should ensure these updates are installed promptly to prevent devices from being attacked due to vulnerabilities.
4. Enhanced Data Monitoring and Analysis: Leverage artificial intelligence and big data technologies to monitor and analyze large volumes of data in real time, identifying potential threats quickly to prevent data breaches and privacy violations.
5. User Privacy Control: Ensure that users are fully informed about the permissions of their devices and can freely choose whether to allow the collection and sharing of their sensitive data.

In this era filled with challenges and opportunities in the IoT field, EELINK Communication has become a key force driving the development of global IoT technology, with 20 years of technological accumulation. As a leading company in wireless communication and IoT solutions, EELINK Communication has earned widespread trust and acclaim through its exceptional innovation capabilities, advanced R&D technology, and global service network.
EELINK Communication not only advances the vision of “everything interconnected” on a global scale but also leverages its robust technical strength to continuously provide secure, efficient, and intelligent IoT devices and solutions to users worldwide. Whether in logistics tracking, vehicle monitoring, or smart manufacturing, EELINK Communication stays at the forefront of technology, leading the future of the industry.
